Healthcare data is among the most sensitive forms of personal information, encompassing medical histories, genetic data, diagnostics, and treatment records. Healthcare organizations are increasingly using blockchain to store and share patient medical data, as blockchain is an immutable, transparent, and decentralized distributed database that can be used to create a trustworthy value chain.
It offers the capacity to overcome operational failures and hacker assaults in a distributive and unchanging manner. Moreover, it gives a record of the data’s ownership and legitimacy. Hence, blockchain is increasingly seen as a general-purpose technology with applications in a variety of sectors and use cases, including healthcare, insurance, supply chain management, and others.
It is important to follow reliable privacy techniques in blockchain healthcare to ensure maximum confidentiality for patient data. You need to develop smart contracts for healthcare privacy when automating data sharing. The ability to encrypt and pseudonymize data stored on a blockchain allows for the protection of personal information while still enabling authorized parties to access essential data.
While it offers transparency and immutability, it is not without inherent vulnerabilities, and healthcare systems must carefully balance these features with strict privacy, security, and regulatory requirements such as HIPAA and GDPR to secure healthcare data on blockchain.
This blog explores the key privacy-preserving techniques used in blockchain-based health data systems and how they enable secure, compliant, and patient-centric data sharing.
Why Privacy Is Complex in Blockchain Healthcare
Traditional blockchains are essentially transparent, allowing every participant to view transactions on the ledger. In healthcare, however, unrestricted visibility is unacceptable. Medical data must remain confidential, selectively accessible, and under patient control.
Yet another challenge to secure healthcare data on blockchain interoperability. Healthcare providers use different systems to store and share patient data, and these systems may not be easy to integrate.
To address these, modern healthcare blockchain architectures rely on a combination of cryptographic methods, off-chain storage, and access-control mechanisms that preserve privacy without compromising the core benefits of blockchain.
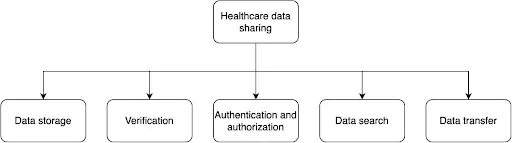
Privacy preservation in blockchain-based healthcare data sharing
Source: Springer Nature Link
Key Privacy Techniques in Blockchain Healthcare Data Systems
- Off-chain Storage for Blockchain Healthcare Data
- Preventing exposure of sensitive patient data.
- Reducing blockchain storage costs (for example, storing 1GB of data directly on Ethereum could cost millions of dollars in gas fees, whereas storing a 32-byte hash costs just a few cents.)
- Ensuring data integrity, as any tampering changes the hash and can be easily detected.
Off-chain storage is one of the most efficient privacy techniques used in blockchain health data systems. Sensitive health records get stored in secure databases or distributed storage systems (such as cloud repositories or IPFS), instead of directly on the blockchain, and only a cryptographic hash or pointer to the data is stored on-chain.
This approach offers several advantages, such as:
This makes blockchain act as a tamper-proof audit layer rather than a data warehouse.
- Permissioned (Private) Blockchains
- Controlled data visibility.
- Better compliance with healthcare regulations.
- Higher transaction throughput and lower latency.
Unlike public blockchains, permissioned blockchains (also known as private blockchains) are distributed ledgers that are not publicly accessible. It gives access only to verified entities such as hospitals, insurers, laboratories, and regulators, as permissioned blockchains require an invitation or a specific grant of authority to participate. Identity management and access rules are enforced at the network level.
Benefits include:
Permissioned networks are particularly well-suited for national health systems and enterprise healthcare consortia.
Permissioned vs. Permissionless
| Feature | Permissioned (Private) | Permissionless (Public) |
|---|---|---|
| Access | Restricted / By Invitation | Open to anyone |
| Identity | Known (White-listed) | Anonymous or Pseudonymous |
| Speed | High (Thousands of TPS) | Lower (Bottlenecks common) |
| Governance | Centralized or Consortium | Decentralized (Community) |
| Trust | Trusted/Vetted entities | “Trustless” (Math/Code) |
- Smart Contracts for Healthcare Privacy
- Granting temporary access to specialists.
- Restricting insurers to billing-related data only.
- Logging all access events for audit purposes.
In private blockchain health systems, smart contract-based access control (SCAC) automates privacy and consent management. Instead of a central administrator manually checking a database to see if you have “Admin” or “User” rights, these self-executing programs define who can access data, under what conditions, and for how long.
Examples include:
This also creates an audit trail, as every time permissions are granted, revoked, or exercised, the event is logged on the blockchain, creating an unalterable history of who accessed what. This ensures transparency and accountability without exposing the underlying data.
- Public-Key Cryptography (PKC) and Encryption
- Secure data sharing between providers.
- Protection against unauthorized access.
- Support for patient-controlled data access.
Encryption is foundational to secure healthcare data on blockchain systems. Patient data is encrypted using public-key cryptography—also known as asymmetric cryptography—ensuring that only authorized parties with the corresponding private key can access the information.
Key features include:
Patients can grant or revoke access to their records by managing cryptographic keys, reinforcing the principle of data ownership.
Also, asymmetric encryption (PKC) is highly secure but computationally “heavy” (slow). To keep permissioned chains fast, enterprises are increasingly using a hybrid system, where PKC is used at the start to securely exchange a “session key,” and symmetric encryption (which is much faster) is then used to encrypt the actual bulk data using that shared session key.
- Data Anonymization and Pseudonymization
- Population health analytics.
- Medical research and AI model training.
- Public health surveillance.
Pseudonymous identifiers are used in blockchain when legal frameworks (GDPR and HIPAA) don’t allow the sharing of actual identities or raw data. Combined with anonymization techniques, this reduces the risk of re-identification. The fundamental difference between the two techniques lies in reversibility, where the link to the data is destroyed forever with anonymization, whereas data can be re-linked with a key in pseudonymization.
In a blockchain, your public key is a pseudonym that doesn’t reveal your identity but lets the network see that you have performed n-number of transactions on a particular day. Anonymization is used for broad analytics where individual identity doesn’t matter, like generalizing birthdate (instead of your actual D.O.B, you just mention age 30-40) or aggregation data (instead of storing individual purchases, you store “1000 units sold in New York”).
Use cases include:
When combined with strict access controls, anonymization allows valuable insights to be extracted without compromising individual privacy.
- Zero-knowledge proofs in Healthcare
- Patient eligibility for insurance claims.
- Compliance with clinical trial criteria.
- Verification of vaccination or test results.
- Audit Trails and Immutable Logs
- Who accessed data?
- When access occurred.
- What actions were performed?
- Detecting anomalous access patterns.
- Enabling privacy-preserving analytics.
- Supporting federated learning models where data never leaves its source.
Zero-knowledge proofs (ZKPs) essentially solve the “Privacy Paradox” in healthcare. It allows one party to prove a claim without revealing the original data. In a permissioned healthcare blockchain, ZKPs usually work alongside off-chain storage (where the actual EHR stays in the hospital’s secure, HIPAA-compliant database), and when a third party asks a question (e.g., “Is this patient over 18?”), a ZKP circuit (like zk-SNARKs) compares the private EHR data against the on-chain hash and generates a proof of the answer.
In healthcare, ZKPs can validate conditions such as:
ZKPs are especially valuable in minimizing data exposure while still enabling trust and verification across organizations.
ZK-SNARKs vs. ZK-STARKs
When implementing ZKPs in healthcare, developers usually choose between these two protocols:
| Feature | zk-SNARKs | Zk-STARKs |
|---|---|---|
| Proof Size | Very Small (fast to verify) | Larger |
| Security | Requires a “Trusted Setup” | Quantum-Resistant |
| Maturity | Widely used (e.g., Zcash, MedRec) | Newer, high scalability |
While privacy is all about restricting access, auditability ensures accountability. Blockchain provides immutable logs of:
These audit trails help organizations demonstrate healthcare blockchain compliance, detect misuse, and build patient trust—without revealing the data itself.
Blockchain and AI for Healthcare Data Privacy
AI can further strengthen privacy in blockchain healthcare systems by:
A combination of AI and blockchain ensures systems are intelligent as well as privacy-oriented.
Designing Healthcare Blockchains with Privacy at the Core with DeepKnit AI
While privacy is the foundation of successful blockchain healthcare systems, robust AI solutions can further enhance their efficiency. Techniques such as encryption, off-chain storage, permissioned networks, and smart contract–based consent make it possible to secure sensitive health data while enabling trusted data sharing.
DeepKnit AI helps healthcare organizations operationalize these privacy techniques through efficient AI-driven privacy intelligence and compliant data ecosystems. By aligning innovation with patient trust and regulatory requirements, DeepKnit AI enables scalable, interoperable, and privacy-first healthcare data ecosystems.
Secure Patient Data with Blockchain and AI.
Partner with DeepKnit AI for measurable health outcomes.