AI in healthcare is making rapid strides. There are numerous tasks an AI-powered Electronic Health Record (EHR) system can handle – from simple and mundane tasks like note-taking, diagnostic data entry and compilation to predicting the onset of critical illness such as diabetes or cardio vascular diseases. Nevertheless, this shift to digital health also gave rise to the relevance of HIPAA compliance in AI-powered EHR systems. As AI continues to revolutionize various aspects of healthcare – from diagnosis to personalized treatment – it’s crucial to consider privacy and compliance.
Enforced by the Department of Health and Human Services (HHS) and the Office for Civil Rights (OCR), the Health Insurance Portability and Accountability Act of 1996 (HIPAA) sets rules and regulations to enhance security in managing sensitive patient data, known as Protected Health Information (PHI), and protect individuals’ privacy.
Clinicians who fail to comply by the HIPAA regulations could attract significant financial penalties, or jail term, and also are at the risk of losing their reputation. In case of wilful violation, the concerned person or organization can even be slapped with criminal lawsuits.
Types of HIPAA Violations
The HIPAA website mentions four different categories of violations which are as follows:

Being the main enforcer, the Office for Civil Rights (OCR) is charged with the duty to investigate complaints of HIPAA violations reported by patients, health plan members, healthcare employees, and members of the public. Periodic audits of HIPAA-covered entities and business associates, and investigation of certain smaller breaches are also conducted by the OCR.
The OCR can impose penalties within a specified minimum and maximum limit per violation under these categories depending on the seriousness of the culpability. However, in cases of suspected HIPAA violation regarding breaches of patient records, the State Attorney General also has the power to investigate.
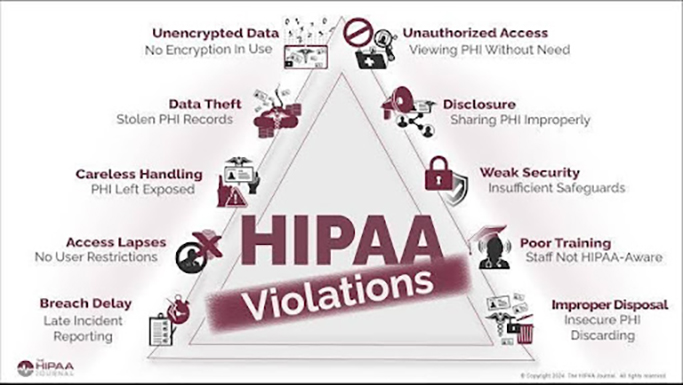
What Are Considered as HIPAA Violations?
One of the major misconceptions associated with HIPAA is that only unauthorized uses or disclosures of PHI are considered a violation. There are many other circumstances in which a covered entity or a business associate can be pulled up for violating HIPAA. The following are the top examples of HIPAA violations in digital healthcare:
- Accessing patient files without authorization
The health records of an individual (PHI) are considered as private and sensitive information, and no one including doctors or healthcare staff, has the right to access it without the patient’s authorization. Even if the information is not used for any ulterior motives, stolen or sold, it cannot be accessed. It has to be noted that only a written consent from the patient is considered as authorization. - Posting PHI on social media (Improper sharing of PHI)
Another common complaint received is regarding medical facilities or individuals posting health information of patients in social media, sometimes as a response to negative reviews. According to HIPAA privacy rules, even if the name of the patient is not mentioned, this is considered a violation as it falls under unauthorized disclosure of PHI. - Failure to do risk analysis (Weak security)
Most of the HIPAA violations occur because the covered entities fail to conduct regular risk assessments and internal audits of access controls and processes. According to the HIPAA privacy and security requirements for ePHI, a risk management plan should include the following:- Evaluate potential risks to ePHI
- Implement suitable security measures to assuage identified risks
- Document the security measures and their justifications; and
- Ensure continuous, adequate security protections
- Failure to train workforce
All covered entities are required to adequately train their workforce on the policies and procedures of the HIPAA guidelines. It is also required to document the training. It will be considered a violation if any of the entities are found not adhering to this necessity. - Improper disposal of ePHI
Medical institutions are supposed to permanently and securely dispose the medical records of patients if they no longer need to retain them. They have to do this in a way so that the medical record is no longer accessible or readable whether they are in printed or digital format. Procedures like shredding or pulping maybe used in case of physical records. Methods like degaussing, physical destruction of portable devices, or data wiping can be adopted in case of ePHI. Institutions failing to do so can attract heavy penalties. - Delay in breach notification
The HIPAA Breach Notification Rule mandates that in the incident of a breach, covered entities must issue notification of the breach to affected individuals, the Secretary of the Department of Health and Human Services (HHS), via the Office for Civil Rights breach reporting tool, and in certain circumstances, to the media. It is also stated that this must be done within 60 days of the incident, and failing to do so will be considered a violation. - Unauthorized disclosure of PHIs
PHIs include all types of patient information be it written, oral or electronic records, and the privacy rule of HIPAA stipulates that an individual has the right to set limitation on its access – as in, who can look into the information, and that too after taking proper consent. Hence, it’d be considered a breach of privacy if anyone looks at, talks about, or shares PHI without the patient’s approval or consent. - Failure to address violation (Careless handling)
The HIPAA security rule stipulates that in the event of an incident involving potential compromise of ePHIs, the covered entity must respond with reasonable steps to mitigate the issue, and ensure that patient information is protected. It is important to have an effective incident response plan to ensure timely notification of a violation while enabling measures to contain its damage. - Medical records getting stolen
It’s very likely for medical practitioners and other healthcare professionals to have their patients’ health information on electronic devices like laptops, mobile devices or laptops. Though this practice is not very safe, it is unavoidable, and there have been many cases of this information getting stolen and shared with unwanted parties. Nevertheless, there are ways to keep the information secured even if your device gets stolen — like encryption, password protection, multi-factor authentication etc. - Non-secure means of sharing PHIs (Unencrypted data)
Hackers and unauthorized individuals are always on the prowl for sensitive information getting shared over unsecured networks. As per HIPAA’s rule book, one can share patient information only through secured networks and that too in encrypted formats, and not via phone calls, texting, video conferencing apps, personal emails and common file-sharing services like torrents.
How to Ensure HIPAA Compliance in AI-driven EHR
Data encryption, access controls, audit trails and secure transmission of data are the main measures to adopt. In addition, regular risk evaluations, strong security protocols and clear policies are vital.
- To safeguard sensitive healthcare data, encryption using strong algorithms such as AES-256 must be used for data at rest. For data in transit, use secure protocols like TLS 1.2+. By implementing role-based access controls, you can limit data access to authorized personnel only.
- Comprehensive audit trails must be established to keep note of all access to and any modifications made to the PHI. Use AI-powered tools to monitor all access logs, distinguish anomalies and enforce access controls. This will help ensure accountability and compliance monitoring.
- Periodic risk evaluations will help identify any vulnerabilities in the electronic health record system. Also, put in place suitable risk mitigation strategies. A comprehensive risk management program must be there for AI-specific risks.
- Secure transmission of data between various systems and devices can be done using proper communication protocols and encryption.
- Make sure to collect, process, and maintain only the minimum amount of PHI required for the AI system.
- An important thing to ensure is that all third-party vendors and partners who handle PHI meet the mandatory security and data protection standards.
- Formulate clear procedures and policies that describe how AI-powered EHR will be used in compliance with HIPAA.
- It is best to appoint a data privacy officer who can be entrusted with overseeing HIPAA compliance and data privacy.
- Security awareness training must be given to your workforce so that they understand HIPAA requirements and best practices.
- Have a strong governance program in place to ensure that your employees, partners, and vendors are all trained in HIPAA compliance and adhere to the applicable policies and procedures.
- Regular audits are the best way to evaluate the success of security measures implemented and identify areas for improvement.
Benefits of HIPAA-compliant AI EHR Systems
The following are the advantages of an AI-powered HIPAA-compliant EHR system:
Real-time Compliance monitoring: AI can continuously monitor an EHR system’s compliance with HIPAA regulations, ensuring real-time detection and correction of any potential violations.
Predictive risk analysis: Healthcare organizations can proactively strengthen their security systems with the help of AI that analyzes past cyber-attacks and predicts potential vulnerabilities.
Automated threat-detection: AI-powered algorithms can proactively detect and flag potential threats even before they occur by detecting unusual patterns in data access.
Smart authentication: AI-driven access controls and advanced biometric authentications can make sure that only authorized personnel have access to sensitive PHI documents.
Conclusion
With the right AI-integrated EHR, healthcare entities stand to benefit considerably. The chosen AI product must be regularly monitored so that it doesn’t introduce any bias or compromise patient privacy. If a breach occurs, make sure to follow HIPAA’s Breach Notification Rule and notify affected individuals, and the HHS. With AI continuing to transform EHR systems, HIPAA compliance and patient privacy must remain a top priority. Integrating strong technical safeguards, enforcing effective administrative controls, designing transparent and accountable AI EHR systems, and promoting ethical oversight are the ways in which healthcare entities can successfully leverage AI’s potential without PHI-related concerns.
Harness AI to revolutionize your business today!
For DeepKnit AI’s solutions for better healthcare documentation.
Contact us